Web 101: Secure Web Practices

Written By Erere Godsent Onyeugbo
The first website was hosted in 1990 by Tim Berners-Lee, a British computer scientist. Since then, it has evolved into a landscape that houses almost all our needs. We shop, we learn, we converse with loved ones, we entertain ourselves, and do much more through the world wide web.
However, rarely do we pause to think of how it may affect us negatively. For something so delicately intertwined with our lives, it is important that we keep it secure.
Keep reading to learn more!
We’ll be taking a look at the following:
- Secure Password Management
- Data encryption
- Web application security
- User education and safe browsing habits
- Backup and disaster recovery
Secure Password Management
Most website home pages come with a layer of security.The most common being passwords. These security features therefore require responsibility of the users. It is common knowledge that the weakest link in security practices is people, therefore user education should be the topmost priority of organizations and individuals seeking to protect their cyber space.
It was previously recommended that passwords should contain a mix of upper and lower case letters, special characters, numbers, or symbols with a minimum of 8 characters in total. However, new research suggests extending the number of characters for increased security.
Now, imagine we had such complex passwords for multiple platforms. Remembering each of them would be daunting, right? This is where password managers come in. It functions as a reservoir to secure store, retrieve, and auto fill passwords.
To take it to the next level, Multi-factor authentication is recommended. This includes adding an extra layer of user identification unique to them. For example, fingerprints, facial recognition, or one time passwords.
Data Encryption
Another cornerstone of secure web transmission is data encryption. What happens in the background, even though we have learned how to be safe using passwords? A website in it’s simplest explanation, involves communication between a client and a server.
The user’s browser is typically the client, and the server is hosted by the website or network provider.
SSL (Secure Socket Layer) and TLS (Transport Layer Security), are cryptographic protocols designed to secure communication over computer networks, between client and servers as previously mentioned. This would ensure that the data transmitted remains confidential and intact.
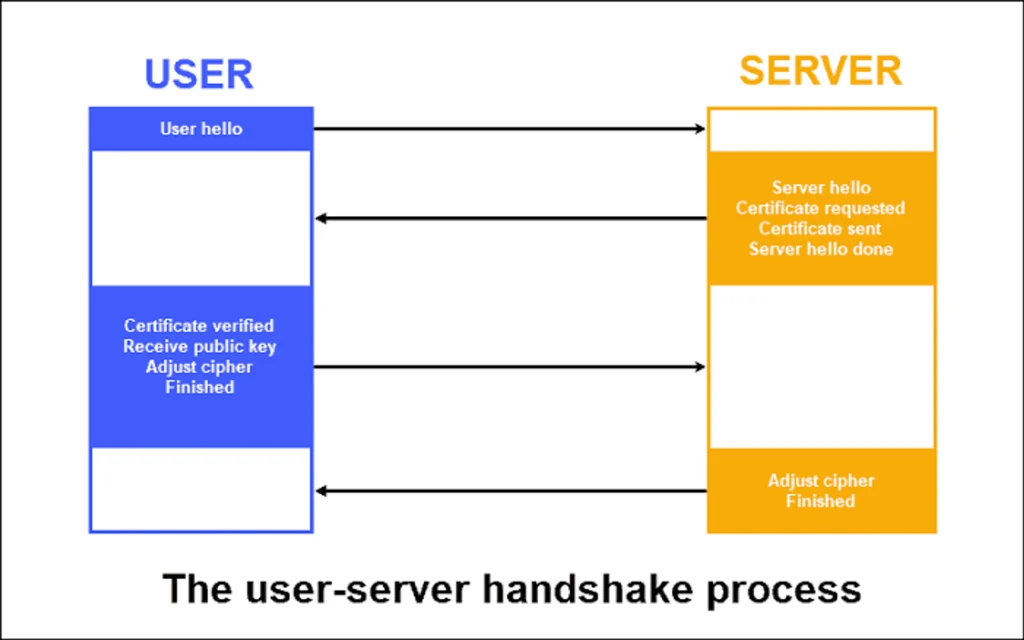
End-to-end encryption exists between users. You may have seen WhatsApp messages notifying you that the chat is end-to-end encrypted. This means the content of the messages can only be witnessed by the parties involved. It also involves a process of encrypting the messages and decrypting it using keys assigned to each user.
Web Application Security
It is important to mention that it is not enough to build a website and call it a day. Maintenance is crucial for all web applications. There are common vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and insecure authentication, that poses significant risks to digital assets.
To prevent these dangers, developers should adhere to best practices for secure coding, as outlined by OWASP (Open Web Application Security Project). Trend Micro Cloud One™ introduces you to application security over here.
OWASP provides a list of guidelines and tools to help developers identify and rectify vulnerabilities early in the development process. Regular testing, including penetration testing and code reviews, is essential to uncover and address security flaws.
Patching is another crucial aspect of web security, as it ensures that known vulnerabilities are promptly fixed. A proactive approach to web application security, combining these practices, helps protect against evolving threats and keeps sensitive data secure.
User Education
As users, we have the responsibility of staying digitally aware. Malicious actors spend time cooking up fraudulent email in phishing techniques. Basic measures to take include:
- Use strong passwords and avoid sharing with anybody
- Add Multi-factor authentication to platforms you frequent
- Change passwords every 3 months
- Avoid clicking on suspicious links. You could also unshorten shorten links with online sites like urlex.org
- Verify the website URL. Look out for padlock symbol at the top left to verify security of the website. Make sure the ‘s’ in ‘https’ is visible and this indicates that the website is secure.
- Employ ad blockers and antivirus software
Note: ‘HTTPS’ simply means transmitted information to the site is safe, not that the website is legitimate. You could be ‘securely’ sending your information to an attacker if the site is illegitimate.
Backup and Disaster Recovery
Imagine this scenario: You wake up to find all your emails and messages cleared. How would you feel?
Data is vulnerable to various threats, including hardware failure, cyberattacks, and natural disasters. Regular backups and disaster recovery planning are critical in the digital realm. The importance of data backups cannot be overstated.
To create an effective backup strategy, prioritize the most important data, establish backup frequency, and store backups securely, ideally in off-site or cloud locations. A well-defined disaster recovery plan outlines steps to take when data loss occurs, ensuring minimal downtime and data restoration.
Conclusion
Web security depends on user education, encryption, secure coding, and vigilance against evolving threats. The digital landscape demands ongoing awareness. Stay tuned for the next part of this series, focusing on secure mobile practices. Happy National Cybersecurity Awareness Month 💓
Cover Image Credit: Web | Caio




