Social Engineering #1: The Sneaky Tactics Targeting Everyday People

Written by Habeeb Kareem
Have you ever received an unsolicited email from a prince in a far-off land, promising you unimaginable wealth in exchange for a simple favour? Or perhaps you’ve encountered a friendly stranger online who seemed a bit too eager to share their personal information with you?
If so, you’ve already taken your first steps into the intriguing world of social engineering, even if you didn’t realize it.
In this article, we will delve into one of the most prevalent threats, accounting for approximately 98% of cyberattacks in today’s world. This article will be a two-part series in which we explore the depths of social engineering to equip ourselves with the knowledge to protect against its subtle and often invisible threats.
Here’s a peek at what we’ll be looking at:
- Social Engineering
- Types of Social Engineering Attacks
- Phishing
- Pretexting
- Baiting
- Quid Pro Quo
- Scareware
- How to Prevent and Protect yourself from Social Engineering attacks
What is Social Engineering?
Social engineering is a crafty form of manipulation that doesn’t require a degree in computer science or hacking expertise. Instead, it preys upon the very fabric of human nature (psychology), relying on our inherent trust, empathy, and desire to help one another.
In other words, it is a deviously clever form of manipulation that exploits human psychology rather than hacking computer systems, with the goal of tricking a victim into handing over sensitive information or granting access to critical infrastructure.
Cyber criminals often employ social engineering tactics (techniques) because it is easier to exploit our natural inclination to trust, than to discover ways to hack into our software. For instance, they might send an email posing as your bank, claiming suspicious account activity. The email urges you to click a link for verification, but it leads to a fake website designed to steal your login details and personal information.
Social engineering can be carried out through phone calls, emails, or text messages, and it usually requires prior knowledge or background information about the target (victim) to establish trust. The individual(s) that employ social engineering tactics are known as social engineers, and both individuals and organizations are tempting targets for them.
Types of Social Engineering Attacks
For the purpose of this article, we will explore only five common social engineering attacks that social engineers use to target their victim(s). They are phishing, pretexting, baiting, quid pro quo, and scareware.
Phishing
It is one of the most common social engineering attacks employed by attackers to deceive individuals or organizations into divulging sensitive information, such as login credentials and financial details. Phishing typically takes the form of an email or text message that appears to be from a legitimate source or entity.
The email or text message typically contains links to malicious websites or attachments with malware (malicious software) and are disguised in a way that creates a sense of urgency, curiosity, or fear in victims.
An example that reflects the real-world dangers of phishing was depicted in the 2001 blockbuster movie, “Ocean’s Eleven”.
A group of skilled criminals, led by Danny Ocean (George Clooney), planned to simultaneously rob three Las Vegas casinos to gain access to the casinos’ security systems and manipulate the vaults. They employed a phishing technique using a deceptive email to trick the casino’s head of security into clicking a link that appears to be a critical software update.
Pretexting
This technique engages targeted victims by using a fabricated scenario (pretext) to increase the likelihood of victims disclosing information or taking actions they wouldn’t typically take in normal situations.
With pretexting, an attacker usually impersonates a representative of a trusted organization to establish trust with the victim. Furthermore, pretexting relies heavily on gathering prior information about the victim before initiating contact.
A classic example of pretexting can be found in the award-winning movie, “Catch Me If You Can”. In one memorable scene, Frank Abagnale (Leonardo DiCaprio) poses as a Pan Am pilot and successfully pretexts his way into various high-security areas at airports without any official pilot credentials.
He was able to accomplish this by leveraging prior information he had gathered from various sources, such as newspapers, to impersonate a trusted representative of his victims’ organizations.
Baiting
Imagine you have a yummy cookie, and you really want someone to take a bite of it. Baiting is kind of like leaving that cookie out where someone can see it and making it look so tempting that they just can’t resist taking a bite, even if they shouldn’t.
From a technical standpoint, the cookie would be a form of physical media (USB drive, CD, or Floppy disk) infected with malware, left in a place (bathroom, elevator, sidewalk, parking lot, etc.) where potential victims are likely to find them, in hopes that the victim would insert it into their personal or work device.
Baiting mostly relies on the curiosity or greed of the victim, which can be poked even further by adding a tempting logo or label on the physical media.
Furthermore, baiting scams are not only carried out in the physical world; they can also occur online in the form of tempting ads that lead to malicious sites, or encourage users to download malware-infected applications.
Quid Pro Quo
It’s a Latin phrase that means “something for something” and this technique is a variation of baiting.
For instance, imagine you receive an email from someone you don’t know, and it says, “Congratulations! You’ve won $1,000! To claim your prize, please click on this link and enter your bank account details”.
In this case, the scammer is using quid pro quo by offering you a cash prize (something they claim you want) in exchange for something they want, which is your bank account details. They’re trying to trick you into giving them your personal information by making it seem like you’re getting something valuable in return.
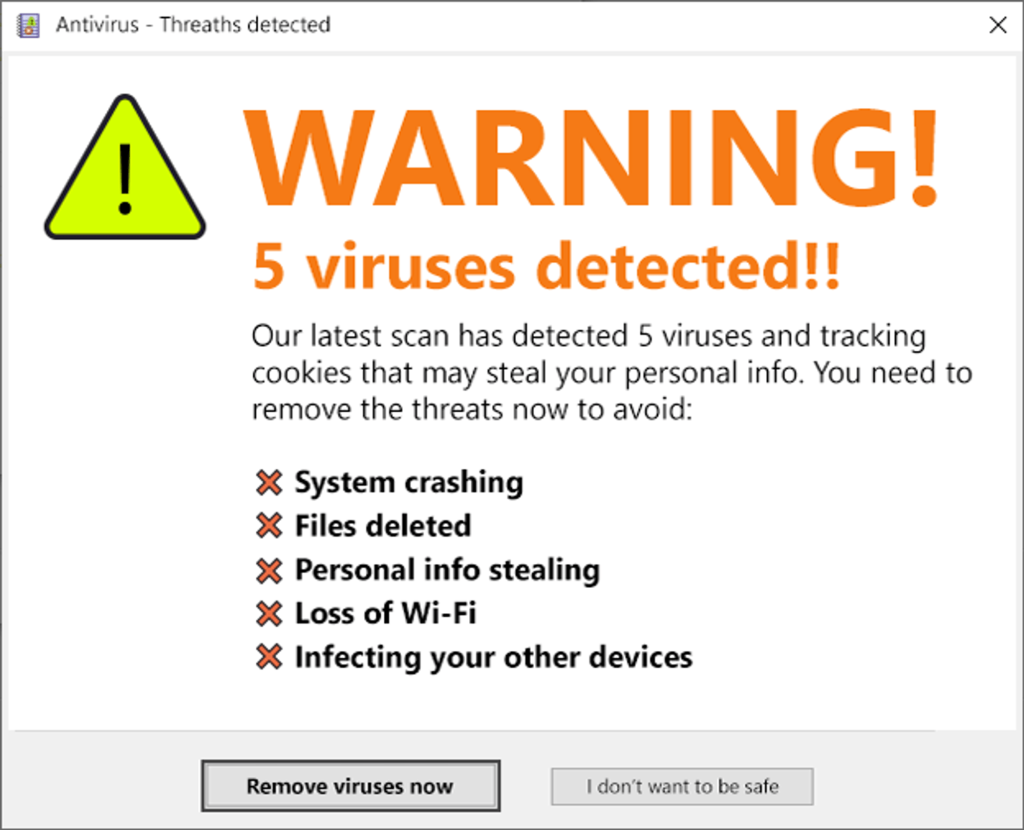
Scareware
It is used by malicious websites to deceive users (victims) into believing that their device is infected with malware, therefore prompting them to install some software (malware disguised as antivirus software) to remove it.
The goal of this technique is to overwhelm users with false alerts (pop-up ads) and threats that will compel them to click on the malicious software.
How to Prevent and Protect yourself from Social Engineering attacks
While it is true that social engineers manipulate human emotions to lure them into traps, we need to be cognizant of these tactics. The best way to prevent and protect ourselves from these attacks is by staying alert and educating ourselves about social engineering techniques.
Here are some tips to avoid being a victim.
Do not open email attachments or links from unsolicited sources
If you receive any unsolicited email with attachments or links from an individual or organization, exercise caution and verify the authenticity of the sender first.
You can quickly do this by checking the email address for spelling errors, or hovering your mouse cursor over links in the email without clicking on them to see the actual URL. For example, “bob@cyséd.org” isn’t the same as, “bob@cysed.org”.
Tools such as QuickEmailVerification, VirusTotal, and Trend Micro’s Email Security Solutions can be used to validate and prevent malicious email addresses, attachments, and links.
Be wary of tempting offers
Be sceptical when you encounter emails, text messages, phone calls, or pop-up ads that promise something that seems too good to be true, as they are most likely scams. Avoid offers that promise large sums of money, prizes, or opportunities without any effort on your part.
Clean up your social media
Social engineers often turn to our social media profiles to find personal or sensitive information (home address, phone number, and financial information) to carry out social engineering attacks. Therefore, it is advisable to refrain from publicly sharing such information.
Exercise caution with urgent requests or solicitations for help
Before responding to urgent requests for assistance from unknown sources, take a moment to consult your inner sense of discernment and verify the legitimacy of such requests before proceeding.
Install and make use of antivirus software
Ensure you have up to date antivirus software installed on your device(s) to help detect and block malicious attachments or links. Check out Trend Micro for freemium antivirus tools and apps.
Beware of typical phishing email subject lines in your spam folder
Some common examples are, “Urgent: Immediate Action Required”, “Win a Prize or Gift Card”, “You’ve Won a Lottery”, or “Free Exclusive Offer”.
Conclusion
As we’ve explored throughout this article, we have seen that social engineering is a multifaceted and ever-evolving threat that manipulates human psychology to gain unauthorized access or information.
Awareness remains our first line of defence. By educating ourselves, staying informed, vigilant, and working together, we can better protect ourselves and our organizations from the ever-present threat of social engineering.
Be sure to stay tuned for the second part of this article, where we will go in-depth into phishing and its types. Until then, stay safe and Happy National Cybersecurity Awareness Month 🫶.
Resources
- 5 most common Social Engineering attacks
- 12 Social Engineering Statistics That Will Make You Question Everything
- Trend Micro Teams Up with INTERPOL To Take Down Notorious Phishing Operation
Cover Image: Social Engineering | Credit: Forta




